1. Source for IP packet structure: https://en.wikipedia.org/wiki/IPv4
2. Source for IP packet structure: https://www.tutorialspoint.com/ipv4/ipv4_packet_structure.htm
3. Illustrated charts from Internet
Figure 1. Structure of an IP packet
"Within an IP packet, the protocol field specifies the type of the current IP packet. If the value is 6, the transport layer protocol is TCP; if the value is 17, the transport layer protocol is UDP. There are other types of transport protocols; we are primarily interested in TCP and UDP in this lab. Given this layered structure, you are asked to extract transport layer information from the trace data once an IP packet is encountered. The general strategy is to read the trace data as you did in your last lab; analyze each Ethernet frame; extract IP and transport layer protocol information; if the transport layer is either UDP or TCP, further dissect the packet to print the detailed information about these two protocols in the packet. The packet formats for UDP and TCP are listed as follows." - CSCI 363
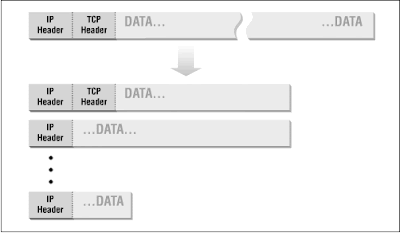
Figure 2. Fragmentation of Data
Source: http://web.deu.edu.tr/doc/oreily/networking/firewall/ch06_03.htm
4. TCP Packet Structure
Source: http://www.eg.bucknell.edu/~cs363/2016-spring/labs/lab10-ip-packet-analyzer.html
5. UDP packet Structure
Figure 3. UDP Packet Header
"The
UDP protocol encapsulates user messages into its own packet structure (Figure
3-2), which adds only four additional fields: source port, destination port,
length of packet, and checksum. Thus, when IP delivers the packet to the
destination host, the host is able to unwrap the UDP packet, identify the
target application by the destination port, and deliver the message. Nothing
more, nothing less."
"In fact, both the source port and the checksum fields are optional fields in UDP datagrams. The IP packet contains its own header checksum, and the application can choose to omit the UDP checksum, which means that all the error detection and error correction can be delegated to the applications above them. At its core, UDP simply provides "application multiplexing" on top of IP by embedding the source and the target application ports of the communicating hosts."
"In fact, both the source port and the checksum fields are optional fields in UDP datagrams. The IP packet contains its own header checksum, and the application can choose to omit the UDP checksum, which means that all the error detection and error correction can be delegated to the applications above them. At its core, UDP simply provides "application multiplexing" on top of IP by embedding the source and the target application ports of the communicating hosts."
Source:
http://www.eg.bucknell.edu/~cs363/2016-spring/labs/lab10-ip-packet-analyzer.html
6. What is the difference between TCP and UDP?
Source: https://support.holmsecurity.com/hc/en-us/articles/212963869-What-is-the-difference-between-TCP-and-UDP-
6a. General
"Both TCP and UDP are protocols used for sending bits of data — known as packets — over the Internet. They both build on top of the Internet protocol. In other words, whether you are sending a packet via TCP or UDP, that packet is sent to an IP address. These packets are treated similarly, as they are forwarded from your computer to intermediary routers and on to the destination."
TCP and UDP are not the only protocols that work on top of IP. However, they are the most widely used. The widely used term “TCP/IP” refers to TCP over IP. UDP over IP could just as well be referred to as “UDP/IP”, although this is not a common term."
6b. Transmission Control Protocol (TCP)
"TCP guarantees the recipient will receive the packets in order by numbering them. The recipient sends messages back to the sender saying it received the messages. If the sender does not get a correct response, it will resend the packets to ensure the recipient received them. Packets are also checked for errors. TCP is all about this reliability — packets sent with TCP are tracked so no data is lost or corrupted in transit. This is why file downloads do not become corrupted even if there are network hiccups. Of course, if the recipient is completely offline, your computer will give up and you will see an error message saying it can not communicate with the remote host."
6c. User Datagram Protocol (UDP)
"When using UDP, packets are just sent to the recipient. The sender will not wait to make sure the recipient received the packet — it will just continue sending the next packets. If you are the recipient and you miss some UDP packets, too bad — you can not ask for those packets again. There is no guarantee you are getting all the packets and there is no way to ask for a packet again if you miss it, but losing all this overhead means the computers can communicate more quickly."
"UDP is used when speed is desirable and error correction is not necessary. For example, UDP is frequently used for live broadcasts and online games."
7. Brief overview of Internet of Things
Based on all descriptions and images in previous sections, you can see that IP is the outer layer of a packet sending over a link or Internet. TCP or UDP is another protocol layer inside of an IP packet to provide communication between a sender and its receiver.
Based on the standard structure of an IP packet, Protocol is an 8-bit field. This implies that there could be 28 - 1 different protocols to be used. Usually it is coordinated by computer industry, thus you cannot freely use or reserve a unique number for your proprietary protocol.
To send a packet to a destination and receiving a reply, a packet must include 2 required parameters, i.e. source address (source IP address) and destination address (destination IP address). In telecommunication, those are called Originating Point Code (OPC) and Destination Point Code (DPC). These 2 parameters are used by routers or switches to deliver or relay a packet.
You can develop your software application with a proprietary protocol, and then use either TCP or UDP packet with your (protocol) data included in the data section of an IP packet before transmitting over the Internet. The receiver would decode the receiving IP packet and removing TCP or UDP header, and extract your (protocol) data in order to process further.
Similarly you could also use wireless communication as a transport medium to relay your IP packet. For example, you could connect your car entertainment unit to an entertainment center using 5G technologies; the Radio Base Station (RBS) receiver only needs to strip off the wireless header and footer, and then relay the IP packet to its destination, i.e. entertainment center. The entertainment center removes the IP's header/footer including TCP or UDP header/footer, and then processes your included data. The entertainment center only needs to reply (example: streaming music) to your car with data in an IP packet with its source IP address and your car’s destination IP address. The router or switches would deliver those to correct RBS, where IP packet would be wrapped up in 5G packets sending to your car over the air. Your car entertainment unit would strip off the 5G wrapping packet’s header and footer in order to extract the intended IP packet and process further.
In most cases, RBS is served as a relay node to transmit an IP packet over the air, thus it won’t remove the IP wrapper to save bandwidth. However, the entertainment center and RBS providers could team up to provide an application together. In this case, the RBS would remove the IP's frame header and footer (or some parameters in IP header/footer) to make its 5G packet smaller. The entertainment unit would not to remove the IP header and footer in its processing. Similarly the entertainment unit doesn’t need to add IP’s frame header and footer (or some parameters in IP header/footer) to make its 5G packet smaller before sending it out via a 5G transmitter toward the RBS, where the missing IP frame header/footer and relevant parameters would be added back before sending over the Internet to the entertainment center. The same methodology would apply to a 5G handset or 5G transmitter/receiver with similar applications functioned as an entertainment unit.
This is basically called Internet of Things (IoT), i.e. any electronic or computer related equipment could be communicated with each other using Internet technologies.
6. What is the difference between TCP and UDP?
Source: https://support.holmsecurity.com/hc/en-us/articles/212963869-What-is-the-difference-between-TCP-and-UDP-
6a. General
"Both TCP and UDP are protocols used for sending bits of data — known as packets — over the Internet. They both build on top of the Internet protocol. In other words, whether you are sending a packet via TCP or UDP, that packet is sent to an IP address. These packets are treated similarly, as they are forwarded from your computer to intermediary routers and on to the destination."
TCP and UDP are not the only protocols that work on top of IP. However, they are the most widely used. The widely used term “TCP/IP” refers to TCP over IP. UDP over IP could just as well be referred to as “UDP/IP”, although this is not a common term."
6b. Transmission Control Protocol (TCP)
"TCP guarantees the recipient will receive the packets in order by numbering them. The recipient sends messages back to the sender saying it received the messages. If the sender does not get a correct response, it will resend the packets to ensure the recipient received them. Packets are also checked for errors. TCP is all about this reliability — packets sent with TCP are tracked so no data is lost or corrupted in transit. This is why file downloads do not become corrupted even if there are network hiccups. Of course, if the recipient is completely offline, your computer will give up and you will see an error message saying it can not communicate with the remote host."
6c. User Datagram Protocol (UDP)
"When using UDP, packets are just sent to the recipient. The sender will not wait to make sure the recipient received the packet — it will just continue sending the next packets. If you are the recipient and you miss some UDP packets, too bad — you can not ask for those packets again. There is no guarantee you are getting all the packets and there is no way to ask for a packet again if you miss it, but losing all this overhead means the computers can communicate more quickly."
"UDP is used when speed is desirable and error correction is not necessary. For example, UDP is frequently used for live broadcasts and online games."
7. Brief overview of Internet of Things
Based on all descriptions and images in previous sections, you can see that IP is the outer layer of a packet sending over a link or Internet. TCP or UDP is another protocol layer inside of an IP packet to provide communication between a sender and its receiver.
Based on the standard structure of an IP packet, Protocol is an 8-bit field. This implies that there could be 28 - 1 different protocols to be used. Usually it is coordinated by computer industry, thus you cannot freely use or reserve a unique number for your proprietary protocol.
To send a packet to a destination and receiving a reply, a packet must include 2 required parameters, i.e. source address (source IP address) and destination address (destination IP address). In telecommunication, those are called Originating Point Code (OPC) and Destination Point Code (DPC). These 2 parameters are used by routers or switches to deliver or relay a packet.
You can develop your software application with a proprietary protocol, and then use either TCP or UDP packet with your (protocol) data included in the data section of an IP packet before transmitting over the Internet. The receiver would decode the receiving IP packet and removing TCP or UDP header, and extract your (protocol) data in order to process further.
Similarly you could also use wireless communication as a transport medium to relay your IP packet. For example, you could connect your car entertainment unit to an entertainment center using 5G technologies; the Radio Base Station (RBS) receiver only needs to strip off the wireless header and footer, and then relay the IP packet to its destination, i.e. entertainment center. The entertainment center removes the IP's header/footer including TCP or UDP header/footer, and then processes your included data. The entertainment center only needs to reply (example: streaming music) to your car with data in an IP packet with its source IP address and your car’s destination IP address. The router or switches would deliver those to correct RBS, where IP packet would be wrapped up in 5G packets sending to your car over the air. Your car entertainment unit would strip off the 5G wrapping packet’s header and footer in order to extract the intended IP packet and process further.
In most cases, RBS is served as a relay node to transmit an IP packet over the air, thus it won’t remove the IP wrapper to save bandwidth. However, the entertainment center and RBS providers could team up to provide an application together. In this case, the RBS would remove the IP's frame header and footer (or some parameters in IP header/footer) to make its 5G packet smaller. The entertainment unit would not to remove the IP header and footer in its processing. Similarly the entertainment unit doesn’t need to add IP’s frame header and footer (or some parameters in IP header/footer) to make its 5G packet smaller before sending it out via a 5G transmitter toward the RBS, where the missing IP frame header/footer and relevant parameters would be added back before sending over the Internet to the entertainment center. The same methodology would apply to a 5G handset or 5G transmitter/receiver with similar applications functioned as an entertainment unit.
This is basically called Internet of Things (IoT), i.e. any electronic or computer related equipment could be communicated with each other using Internet technologies.



No comments:
Post a Comment